Conformity Data Security Standards
A commitment to data security by adhering to recognized standards and frameworks. Keeping confidentiality, integrity, and availability of data by implementing policies, procedures, and controls.
A commitment to data security by adhering to recognized standards and frameworks. Keeping confidentiality, integrity, and availability of data by implementing policies, procedures, and controls.

Vision
To become a leading cybersecurity and information security partner, protecting enterprises by harnessing data protection and contributing to a secure global business environment. Aim to integrate best practices, empower organizations to manage risks, and enhance their global competitiveness.
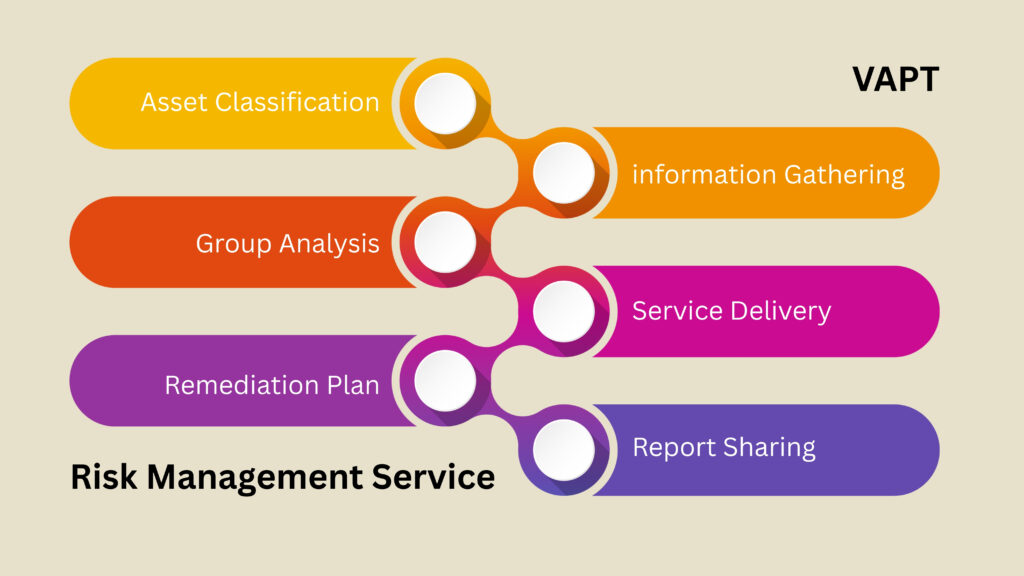
It involves analyzing risks’ likelihood and impact, developing strategies to minimize harm, and monitoring measures’ effectiveness.
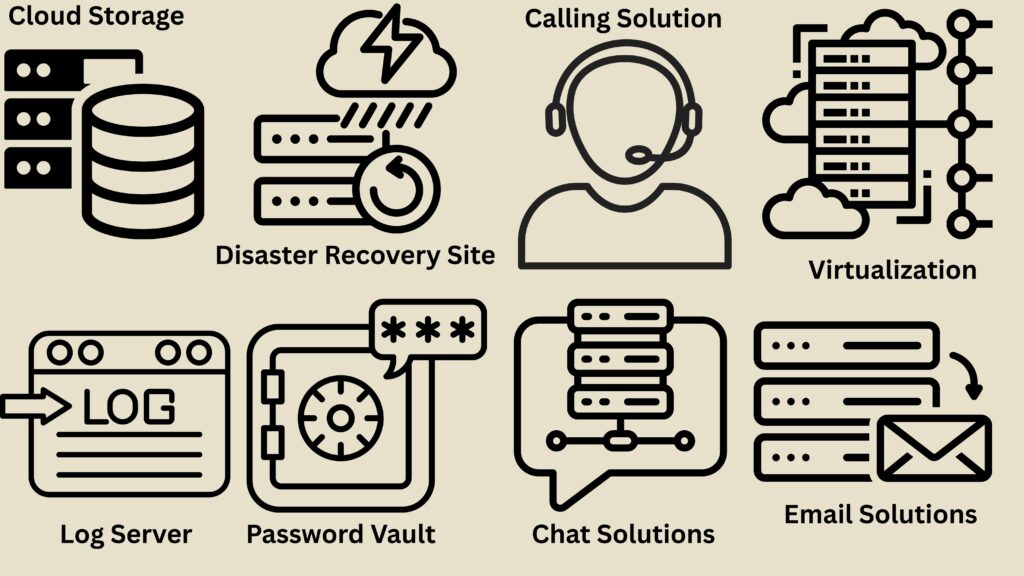
An effective data process management is not just about managing data, but about leveraging it as a strategic asset to drive business value and success.
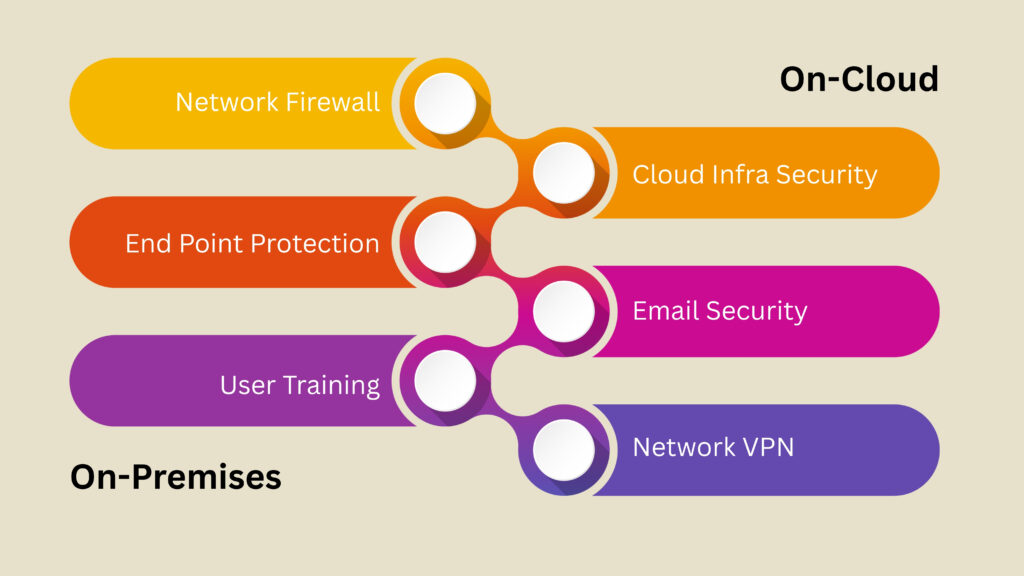
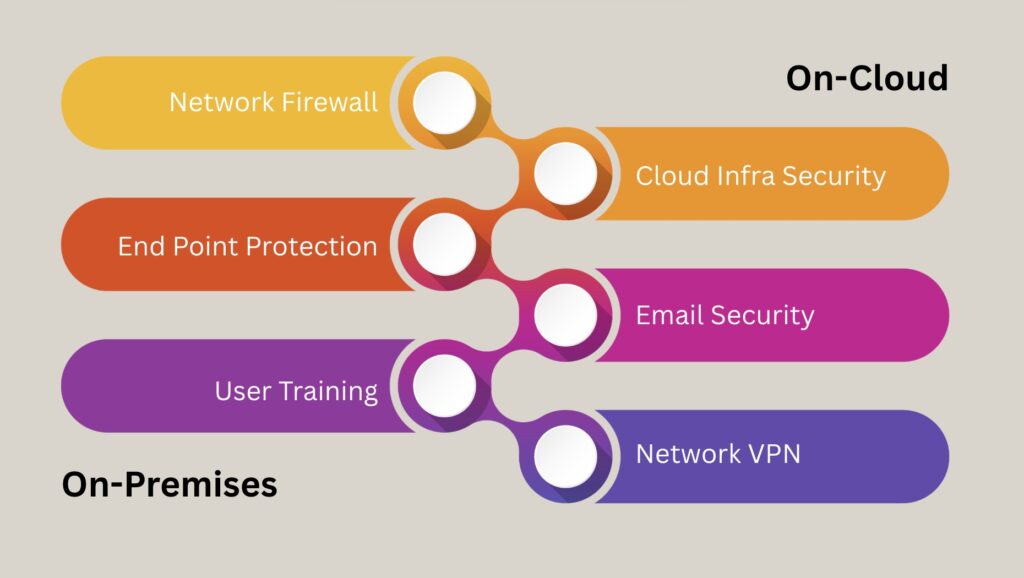
By implementing a combination of technical, administrative, and physical security controls, organizations can significantly improve their data security posture and protect their sensitive information from a wide range of threats.

General Data Protection Regulation (GDPR), EU

Privacy Act 1988 (APP’s), Australia

Privacy Act 2020 (IPP Act, 2020), New Zealand

Personal Data Protection Act 2012, Singapore

Digital Personal Data Protection Act 2023, India

Federal Decree Law No. 45 of 2021 (PDPL), UAE
CyberSecurity
The goal is to identify, control and minimize impact of uncertain events. The objective of risk management is to reduce risk to an acceptable level.
Importance:
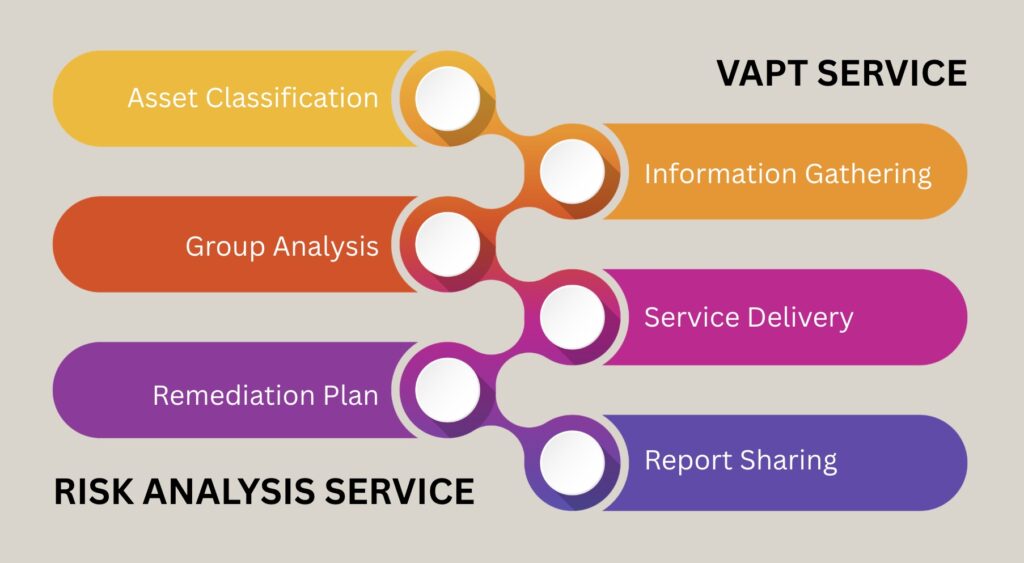
Organisation
It the systematic approach to handling data throughout its lifecycle within an organization, it encompasses the processes of collecting, storing, organizing, securing, and utilizing data to ensure its accuracy, accessibility, and overall value for business operations and decision-making.
Importance:
DataSecurity
Our services encompass a wide range of solutions designed to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. These solutions can be categorized into technical, administrative, and physical security controls.
Importance:
Technical security controls include:
Administrative security controls include: